Cyber security for the infrastructure
Cybersecurity for businesses is of paramount importance. All aspects of IT security must be taken into account to minimize the risk of cybersecurity threats. Data theft, industrial espionage, sabotage and blackmail must be prevented at all costs.
In short, practical solutions are in demand. IT security software that enables automatic detection and monitoring of IT landscapes and thus reduces the manual administration effort.
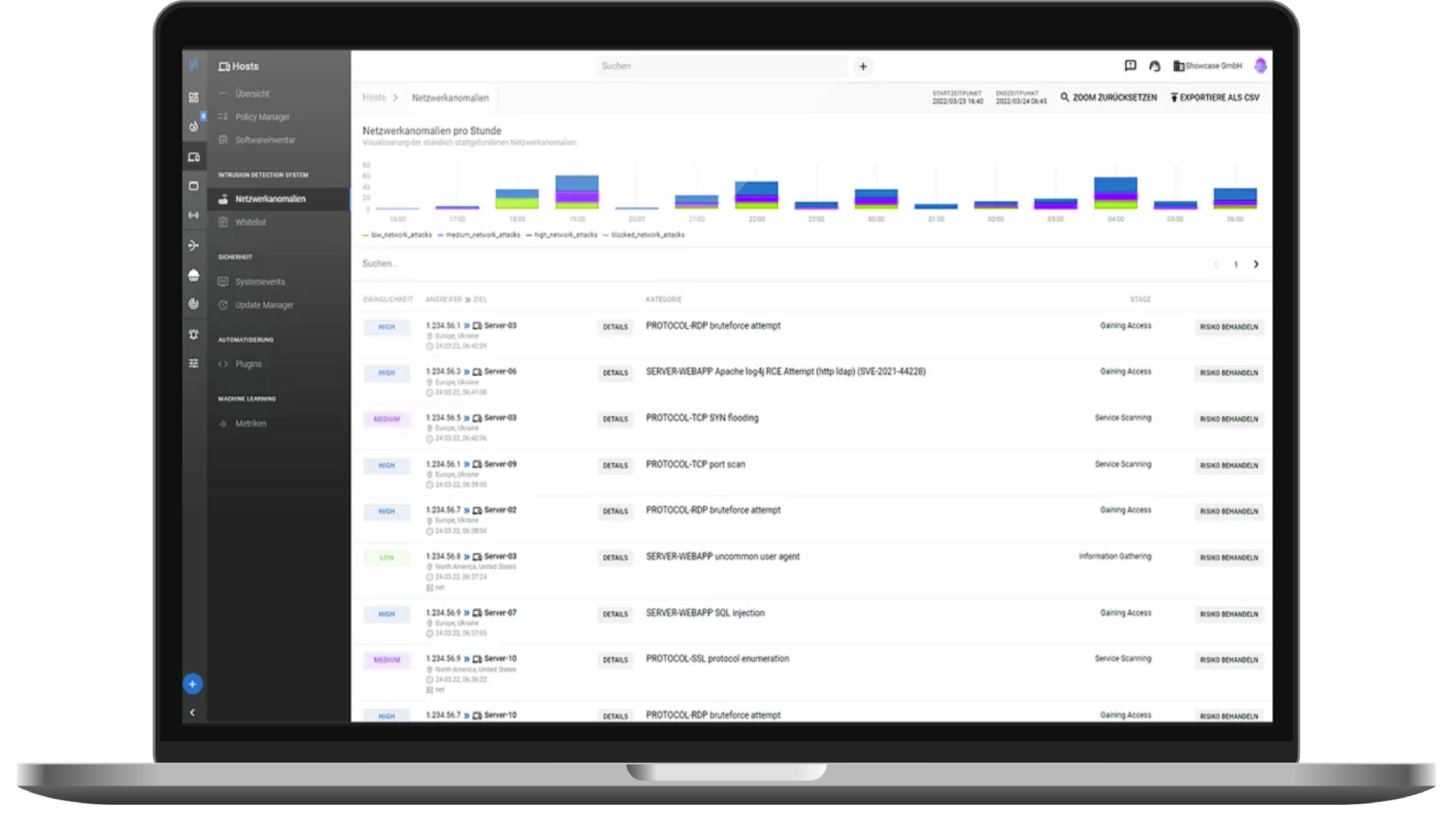
This first involves an inventory of all servers and endpoints in the IT infrastructure, followed by permanent scanning of the IT environment for a live picture of its condition. By actively and comprehensively monitoring and securing all servers and ed devices, vulnerability management identifies security gaps, missing updates and inadequate configurations for immediate remediation. Web applications such as websites are also fully monitored in terms of availability and security.
Using automated penetration tests, you audit your systems regularly and detect possible entry gates for hackers at an early stage. System events in the event of an alarm are responded to in an automated way, which relieves the IT department.
IT security is critical:
Full transparency
Every server and endpoint in the IT network is detected, continuously analyzed and "taken care of" according to the exposed threats.
Maximum control
Security vulnerabilities, missing updates and insufficient configurations are detected via vulnerability management
Active health monitoring
Applications (services) and device connections are actively monitored. With automated penetration tests, the own IT system is audited continuously.
Weaknesses in the IT-infratructure
- Missing inventory of all servers and endpoints with live image over health
- Missing active monitoring of devices for security vulnerabilities, updates and configurations
- Missing application monitoring with attack detection and blocking
- Missing auditing of own system with automated penetration testing
Risks that result
- Increased vulnerability to cyberattacks
- Loss of sensitive data and intellectual property
- Business and financial losses due to system disruptions
- Large amount of time and resources spent on troubleshooting by IT operations
Service of Rey
- IT inventory (asset discovery)
- Vulnerability management
- attack detection and blocking
- IT monitoring of network infrastructure
- Automated penetration testing
- Website monitoring
Want to know more?
Sandro Gloor will be happy to show you,
what benefits you can achieve in your company.
sandro.gloor@rey-technolog.com
+41 58 810 04 81